By now, most of us have heard of Zero Trust and how its framework seeks to protect data across every access point by reaffirming trust in a user’s identity. According to Mimecast, a Zero Trust Architecture allows security professionals to ‘safely manage security across complex cloud environments, regulatory requirements, and workflows’, which is probably the reason why it’s now considered to be the aspirational ideal by many.
Differing from the traditional approach of securing the perimeter around a network, Zero Trust does not trust the user logging in, but rather, assumes their identity can be compromised. In doing so, it applies the ‘least privilege’ principle through multi-factor authentication. What does this mean? Essentially users must provide additional validation to access higher point privileges, such as access to certain data. The architecture operates by evaluating the user’s profile against the sensitivity and context of the asset they are seeking through their geolocation and even the operating device.
The Core Requirements of Zero Trust
Below are the core requirements the Zero Trust architecture acknowledges to safeguard and simplify workflows, as identified by Mimecast:

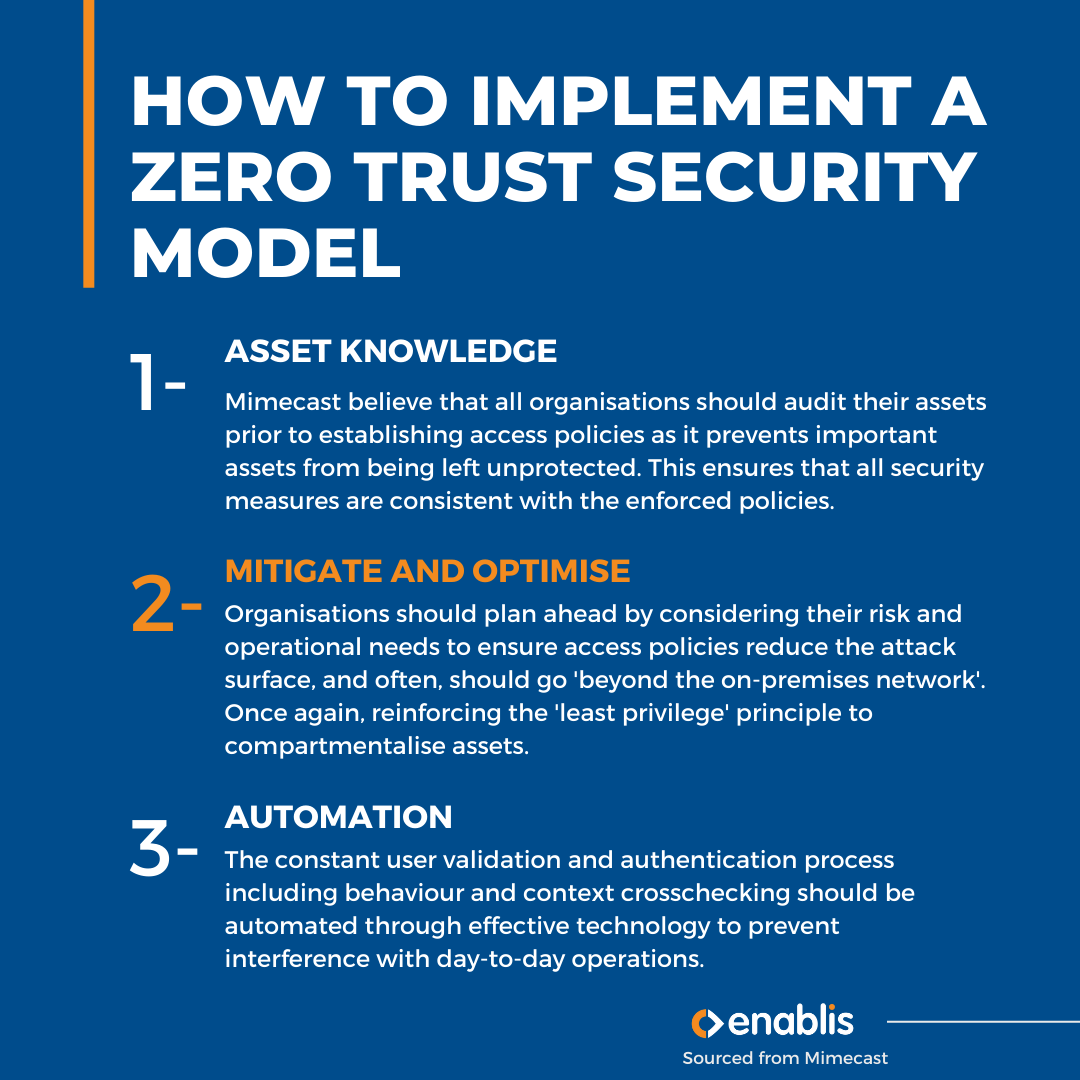
Implementing a Zero Trust Security Model
Mimecast believes that the Zero Trust model should be ‘approached as a philosophy’, and rather than being implemented as a singular tool, it should be integrated alongside multiple vendors’ tools.
The Benefits of a Zero Trust Framework
Despite there being no tool that offers 100% protection against cybercriminals, the Zero Trust Framework has been effective when it comes to addressing many of the challenges we see today.

If you would like further information you can also visit our Zero Trust page here or click here to get in contact with one of Enablis’ security experts.

