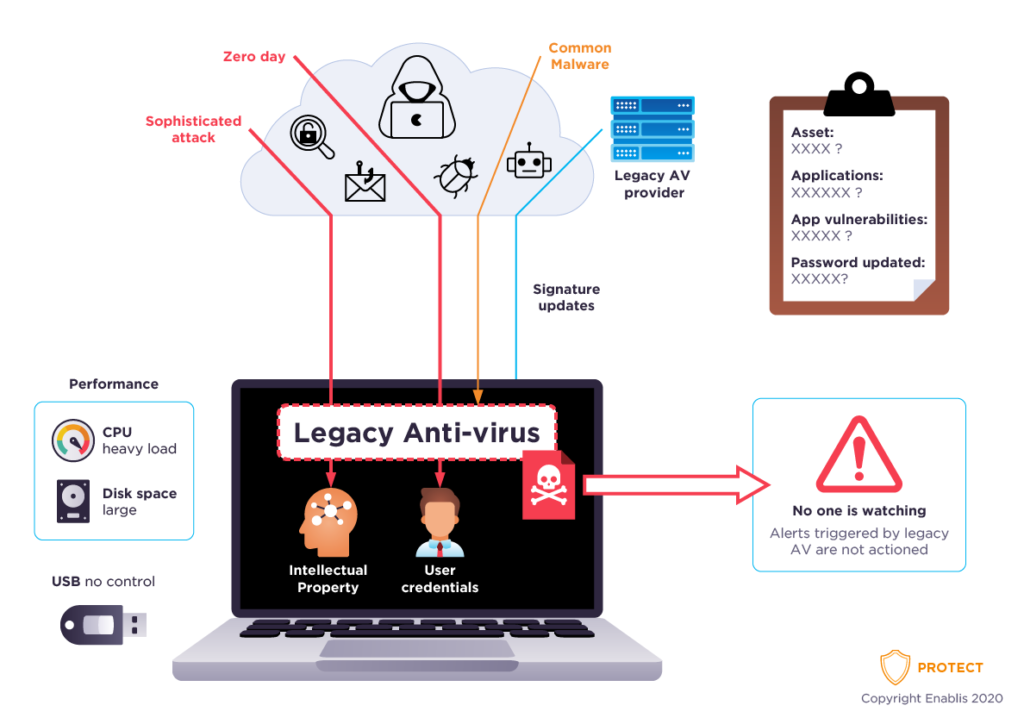
Endpoint Protection will ensure your business is not exposed to threats and cyber attacks
Many organisations have very complex security requirements and are using legacy solutions that are ineffective against modern threats.
These are:
- Costly to deploy
- Difficult to maintain
- Have heavy CPU usage
- Don’t protect the business from Zero attacks
- Alerts triggered by legacy AV are not actioned
- App and password vulnerabilities
- No USB control causing reduced security
Even when existing security solutions are upgraded, they unfortunately are not stopping attacks and are ineffective against today’s sophisticated threats. As current complex solutions are harder to manage, they tax the endpoints to the point where employee productivity is reduced.
Enablis Endpoint Protection
IT executives and legacy vendors are faced with multiple challenges and are continually being asked to add more security components to an already complex solution that’s not effectively stopping attacks and breaches.
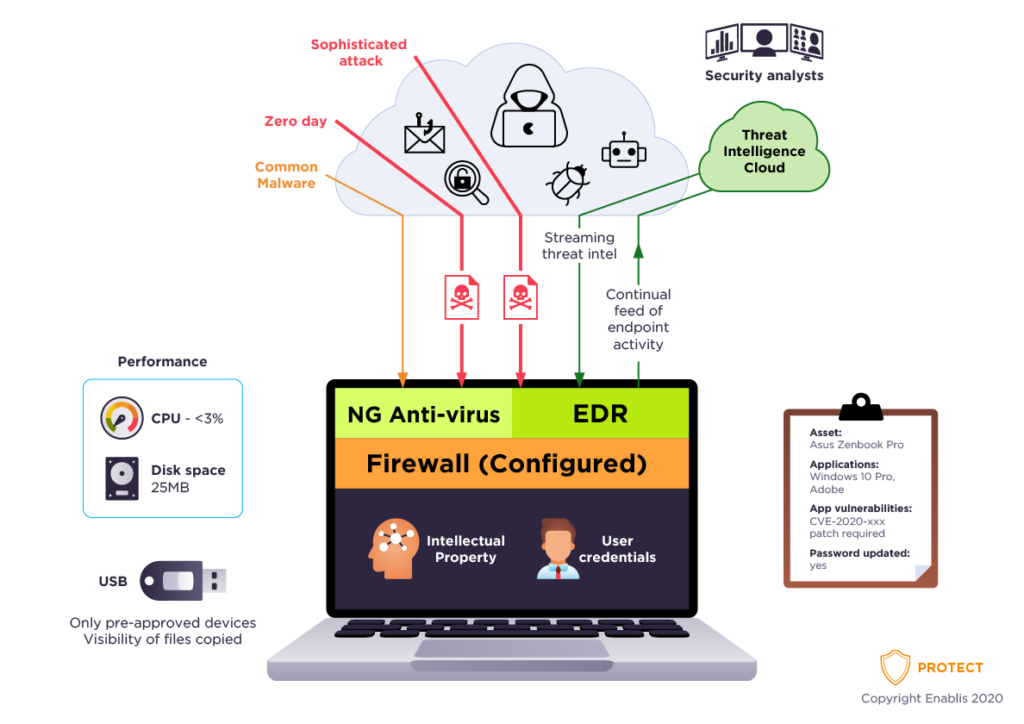
Enablis partners with the leader in cloud-delivered endpoint security – leveraging artificial intelligence (AI), and a platform offering instant visibility and protection across the enterprise. This platform prevents attacks on endpoints on or off the network. It is deployed in minutes to deliver real-time protection and actionable threat intelligence from day one.
Enablis Security experts seamlessly unify next-generation AV with best-in-class endpoint detection and response, backed by 24/7 managed threat hunting. The cloud infrastructure and single-agent architecture takes away complexity and adds scalability, manageability, and speed to protect your business.
Here’s how you can you be effective in stopping data breaches
The Enablis team will work with you to protect your business against all cyber attack types, using sophisticated signatureless AI and Indicator-of-Attack (IoA) based threat prevention to stop known and unknown threats in real time.
Our Endpoint protection will provide:
- Next-Generation
Antivirus
- USB Device Control and visibility
- IT Hygiene
- Endpoint Detection and response 24/7
- Firewall Management – Hosted
- Firewall Control
- Threat Hunting
- Incidence response and proactive security services
How can you be effective in stopping data breaches ?
Enablis and CrowdStrike will protect your business against all cyber attack types, using sophisticated signatureless AI and Indicator-of-Attack (IoA) based threat prevention to stop known and unknown threats in real time. Powered by the CrowdStrike Threat Graph™, Falcon instantly correlates 2 trillion security events a week from across the globe to immediately prevent and detect threats.
* Taken from the CrowdStrike website 2020
Tips to secure today’s newly distributed workforce
COVID-19 has caused a level of social and economic upheaval that is unprecedented in modern times. Organisations are facing sudden and profound challenges as they seek ways to quickly support corporate directives for employees to work from home. This rapid, global exodus from the office poses considerable challenges for organisations as they strive to maintain security across their newly remote workforce.
An eBook from Crowdstrike, “Securing Today’s Distributed Workforce: Resources for Ensuring Optimal Security During the Global Pandemic,” covers a wide range of topics including best practices and recommendations that can help your organizations ensure security across all your users with speed and efficiency.
Cybersecurity remains mission-critical to organisations, regardless of size. In these current challenging times, organisations need to focus on business resiliency, while reassuring employees and customers that they are protected, so they can continue to focus on the things that matter most.
Download the Securing today’s newly distributed workforce ebook
Download this eBook – Securing today’s newly distributed workforce for important information on:
- The cyberthreats that are heightened by the COVID-19 crisis and how to protect against them
- The important role of prevention tools and why the cloud is crucial for maximizing your security
- The role patch management and accountability play in securing a remote workforce
- Why remote incident response and endpoint recovery are critical capabilities
- Recommendations for ensuring optimal security across your distributed workforce during the COVID-19 crisis

Look at the analysis of the top Cyber Threat Trends in 2022
The CrowdStrike 2022 Global Threat Report is one of the industry’s most anticipated reports and trusted analyses of the modern threat landscape and adversary universe.
Developed based on the firsthand observations of the CrowdStrike Intelligence team and Falcon OverWatch™ elite threat hunters, combined with insights drawn from the vast telemetry of the CrowdStrike Security Cloud, this year’s report provides crucial insights into what security teams need to know — and do — in an increasingly ominous threat landscape.
The report highlights the observed trends and explores real-world scenarios from 2021 and offers practical recommendations to protect the people, processes and technologies that drive the modern enterprise, including:
- How state-sponsored adversaries target IT and cloud service providers to exploit trusted relationships and supply chain partners
- How state-sponsored adversaries weaponise vulnerabilities to evade detection and gain access to critical applications and infrastructure
- How sophisticated adversaries are exploiting stolen credentials and identities to amplify ransomware big game hunting attacks and infiltrate cloud environments
- How malicious actors are intensifying attacks on critical cloud infrastructure with new, sophisticated approaches
- How organisations can protect themselves from all of the above — and more
*Taken from the CrowdStrike Report

In-depth analysis of the top cyber threat trends over the past year
The CrowdStrike 2021 Global Threat Report is one of the industry’s most highly anticipated reports on today’s top cyber threats and adversaries. It features analysis from the CrowdStrike Threat Intelligence team and highlights the most significant global events and trends in the past year.
The report covers real-world scenarios and observed trends in attackers’ ever-evolving tactics, techniques and procedures and offers practical recommendations to protect your organization in the coming year. This year’s highlights include:
- The COVID-19 pandemic and its effect on cybersecurity
- “Big game hunters” targeting the healthcare sector
- Significant nation-state-based targeted attacks and operations observed from China, Iran, DPRK, Russia and others
- The pivotal role that access brokers play in the eCrime ecosystem
- How ransomware adversaries are rapidly adopting data extortion methods
- Recommendations you can take to proactively address emerging threats
*Taken from the CrowdStrike Report

A Proven approach to cloud workload security
Download the White Paper As a cybersecurity company that has built one of the biggest cloud architectures in the world, CrowdStrike has gained an exceptional vantage point and garnered unique experience on what it takes to secure cloud workloads.
This white paper shares some of the knowledge and experience the CrowdStrike team has gained from securing its own cloud. It begins by describing the major factors that make the cloud vulnerable to threats and sharing some security-related observations made by the CrowdStrike cloud team.

It then explains CrowdStrike’s approach to protecting a cloud infrastructure that is processing trillions of events per week and continues to grow as the company adds new capabilities to the Falcon platform and gains new customers. The paper concludes by describing the role the Falcon platform can play in protecting cloud workloads.
Download the Whitepaper to understand
- The reasons behind breaches in the cloud
- The trends CrowdStrike has observed from securing one of the world’s largest cloud platforms
- The three-pronged security strategy CrowdStrike uses to guide its cloud security initiatives
- How the CrowdStrike cloud-native platform protects all workloads, regardless of their location
Benefits of a robust Endpoint security solution
Improved security
Improved security
Enable zero trust network access
Enable zero trust network access
Enable new digital business scenarios
Enable new digital business scenarios
Increased effectiveness of
network and network security
Increased effectiveness of
network and network security
Improvement in
performance/latency
Improvement in
performance/latency
Centralised security policy with
local enforcement
Centralised security policy with
local enforcement
Working with a trusted Endpoint Security Partner
Over 16yrs security &
network design & implementation
Technical expertise
managing complex security frameworks
Proven capability & success delivering
complex security solutions
Award-winning Managed
Service Provider
Cyber security specialists
Leading end to end security solutions
provider at competitive prices
Provide ongoing security
maintenance and management
Visibility – in-depth Security,
application performance reporting
24×7 proactive service
and support
Enablis Security Vendor Partners












