The COVID pandemic has brought about the need for organisations to accelerate the adoption of cloud technologies in order to adapt to today’s hybrid workforce model.
Businesses now need to provide employees with the flexibility to work from any location. From a simplistic point of view, cloud adoption is the obvious choice, as it allows organisations access to their applications and data from anywhere at any time. Modern cloud adoption enables workforces to work and collaborate more efficiently, regardless of their location.
Today’s Challenges
The challenge of hybrid working for all businesses is how they can enable secure access to data for staff, partners and customers. The current challenge is the capability to provide what the business requires in a secure manner without overloading the organisation’s infrastructure and operations teams, and without sacrificing end-user performance and satisfaction.
Traditionally, companies were able to follow a perimeter-based security approach, where there was a clear delineation between what is trusted and what is not. Most of the applications, data and workforce were within the businesses own control or inside a “safe perimeter” (e.g.,a Data Centre or physical office).
We now have more users, devices, applications, services, and data located outside the organisation than inside. Data is ubiquitous so its effectively stretching the perimeter concept to the point that it becomes almost non-existent, and every connection, user, or service must be treated as a potential threat.
Furthermore, organisations need to ensure an optimal and seamless end-user experience from any location regardless if they are remote, working in a home office or from a branch office.
These complexities and challenges are the reality that IT leaders are now facing and they need to find the right balance between security and user experience that aligns to their strategy to reduce the business risk profile and align to corporate objectives with finite resources and budget.
What’s the difference between SD-WAN & SASE?
Software Defined WAN (SD-WAN) has been the preferred technology to address network performance challenges since businesses started to embrace public cloud services long before the hybrid workforce became the norm.
As more applications are being consumed from the Internet, the old “safe perimeter” MPLS-based architecture where all internet traffic was centralised through a single Data Centre or location is no longer fit for purpose for today’s business requirements and for modern workers
SD-WAN’s driving principle is to facilitate cloud connectivity and simplify the operational environment, by centralising the control and management of the network on a single software plane -providing dynamic, policy-based, application path selection across multiple network connections (e.g., broadband, wireless, ethernet, etc.). This allows traffic to flow directly from the branch office to the internet.
For all of its benefits, SD-WAN only addresses the branch network, as it only covers site-to-site connectivity and internet access to public cloud services.
SD-WAN does not protect the mobile workforce, nor today’s security requirements across an organisation’s environment.
As a consequence, in an attempt to address those gaps, organisations tend to implement multiple technologies from different vendors, resulting in a combination of incongruous parts (e.g., multiple policies, logs, interfaces), hence increasing administrative and operational complexities
How SASE comes into the picture
This is where Secure Access Secure Edge (SASE) comes into play. As per Gartner’s definition, “SASE delivers converged network and security as a service capability, including SD-WAN, SWG, CASB, NGFW and zero trust network access (ZTNA). SASE supports branch office, remote worker and on-premises secure access use cases."
SASE provides an identity-aware and context-aware network and security access fabric that connects users, devices and locations everywhere (see the below Gartner left side of Figure 1) to the enterprise’s digital resources anywhere (see the right side of Figure 1).
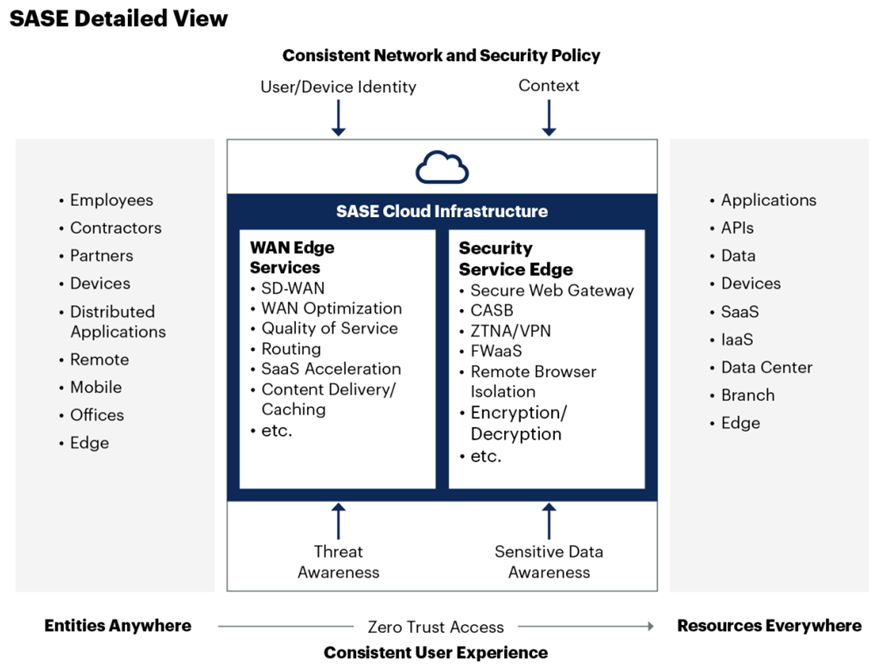
SASE addresses the challenges of the “hybrid world”, infrastructure and workforce, by providing secure access to the organisation’s data and applications everywhere (on-premise, cloud, SaaS) for any user regardless if they are remote, home office or branch office users.
A SASE framework provides organisations with a centralised view of their entire environment, providing them with the ability to apply and maintain consistent network and security policies and to quickly identify any deviations or gaps in the organisation’s security posture.
SASE is a journey that encompasses both security and networking, therefore there is no specific blueprint to follow when implementing this new approach, making it critical to develop a long-term strategy with short-term milestones to cover both current and future requirements.
Depending on where an organisation is within its security and networking programs, the SASE journey can start by addressing a single or a couple of elements of an organisation’s environment, including securing the mobile workforce, replacing a web proxy or implementing SD-WAN, giving businesses the flexibility to support short term needs, without compromising their future strategy.
It is important to highlight that Gartner recommends “to choose single-vendor SASE offerings that provide single-pass scanning, single unified console and data lake covering all functions to improve user experience and staff efficacy”, making a compelling case for businesses to consider consolidation when embarking on the SASE journey.
SASE business benefits include:
- Reduced cost and complexity by consolidating the network and security stack in one platform
- Support for branch, remote and mobile users.
- Provides a holistic view of an organization’s network and security so the organization can better protect it.
- Enable companies to consistently apply security controls increasing their security efficacy.
- Allows users to immediately gain secure access to a company’s network, wherever they are and whatever device they use.
If you would like further information visit Enablis' SASE webpage here or click here to get in contact with one of Enablis’ SASE certified experts.
This blog has been written by Luis Urbaez, CTO Enablis.

