As we ve mentioned in a previous blog, Zero Trust Network Access (ZTNA) can be defined as a framework where all users must have continuous authentication, authorisation and validation prior to data and application access. We ve also examined why Palo Alto Networks believe ZTNA 2.0 is the superior option when it comes to identity protection, as it s capable of ensuring 'true end-to-end multitenancy' by providing 'proactive identification of problems, along with the ability to isolate and resolve issues automatically to ensure the best possible experience .
With organisations focused on scaling any existing virtual private networks (VPNs) to accommodate for remote workers, it s become apparent that simply using a VPN is no longer satisfactory when it comes to ensuring a secure connection, and providing complete security for a remote workforce.
This is where ZTNA 2.0 comes into play as a ZTNA 2.0 framework has the advantage of being able to securely support workers regardless of where they want to work- on premise, in the comfort of home or travelling.
When it comes to implementation, Palo Alto Networks discovered that 98% of CXOs admitted the implementation process to be somewhat challenging. In short, those challenges can be attributed to prioritisation uncertainty, unqualified vendors being unable to provide a complete integrated solution, and lack of expertise internally.
Let s take a look at what a ZTNA 2.0 implementation process looks like with Palo Alto Networks:
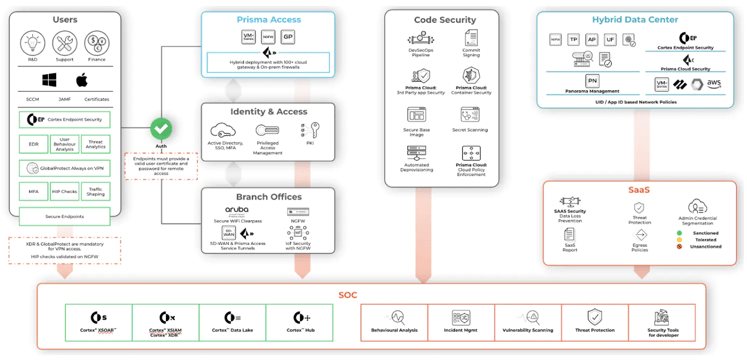
The 5 key lifecycle principles for ZTNA 2.0:
- Enforces least-privileged access: ZTNA 2.0 is independent from IP addresses and port numbers to enable accurate access control.
- Trust verification is a continuous process: ZTNA 2.0 continuously monitors the users behaviour, application behaviour and device posture for a trust assessment.
- Security inspection is continuous: ZTNA 2.0 continuously inspects application traffic which is instrumental when preventing threats.
- Data is consistently protected: ZTNA 2.0 also implements a single data loss prevention policy which is useful when it comes to providing a consistent control of data regardless of its application.
- All applications are secured: ZTNA 2.0 provides protection across various applications inclusive of ‘modern cloud-native applications, private legacy applications, and SaaS applications .
If you would like further information visit Enablis' Zero Trust webpage here or click here to get in contact with one of Enablis security experts.

